Cyberattack, Spyware in 2 Battleground, Israel - Palestine and Russia - Ukraine
manipulating OSINT, manipulating bombing, 'honey trap' in dark web.
Gaza - Kyiv - Tel Aviv 9.56am
When Russia invaded Ukraine in 2021 the hacktivist group Anonymous declared a cyber war against Russia. I conducted extensive research into the methods, tactics, and results of how a group of semi-unorganized non-governmental hacktivists were able to cause major havoc in Russia.
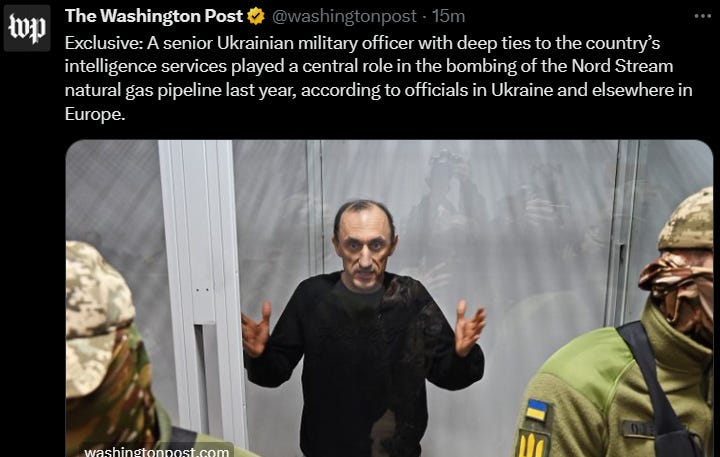
Old enough to remember that everybody in Europe was so sure last year that Russia had itself sabotaged the Nord Stream pipeline. Or Russia send a cyberattack to camouflage Nord Stream. The 13 months investigation by the Washington Post found that Ukrainian military officer coordinated Nord Stream pipeline attack that shocked and mystified the West. Endangered supply of energy for Europe, although entire Europe hate Russia.
It was the first time the world saw a successful crowdsourced cyber war that defenders could not track back to any specific country or government.
In the more recent conflict between Israel and Hamas, I have seen hacktivist groups attempt many of the same techniques that were successfully used against Russia. In the 19 months since hacktivists declared cyber war against Russia, cyber security experts and intelligence services around the world have had time to analyze, prepare, and try to insulate themselves by learning from the failures of Russia’s cyber defenses.
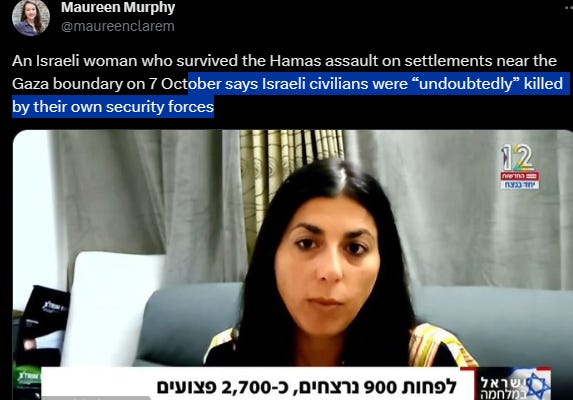
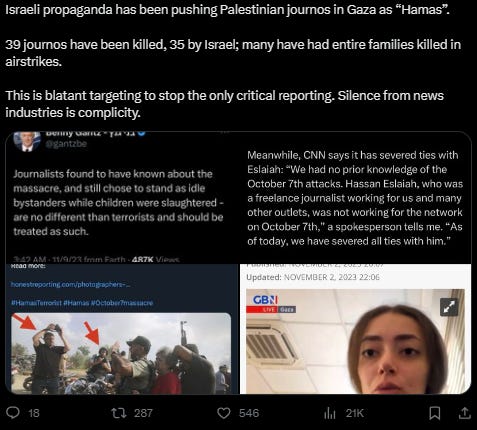
The U.S. intelligence community has growing confidence that reports on the death toll from health authorities in Hamas-controlled Gaza are roughly accurate, U.S. officials said, according to WSJ.
CIA Director Richard Burns already in Doha Qatar since Friday and still in Doha right now, for a lot of ‘intelligence meeting’, such as with Mossad. The situation in Gaza really grim, and even CIA Director must flying from Virginia to the Middle East. At least Israeli killing 80 hostages with indiscriminate bombing in Gaza, don’t know detail of citizenship of 80. More and more footage IDF killing a Kibbutz resident, not HAMAS, with [also] indiscriminate bombing and firing.
Cyberspace acts now as a second front with no defined rules of engagement. Hacktivists and government-affiliated groups can choose a side and launch numerous attacks based on their specific skill sets, tipping the scales of the conflict with seemingly just a few clicks. These attacks serve as a warning to nations and businesses alike that we should all prepare for future attacks and implement proactive cybersecurity measures. Going forward, the same potential threats apply to corporations, private businesses, and individuals.
Here are the biggest threats I have seen that U.S. companies should look out for as the Israel-Hamas war rages on and the Russia-Ukraine conflict continues:
Denial of service: DoS attacks against private businesses and government entities can come from all over the world and simply flood websites with an overwhelming volume of traffic requests. This “bad traffic” consumes the network’s resources — such as bandwidth, processing power, memory, or network connections — and leaves virtually no capacity for legitimate user requests, hence the term Denial-of-Service. DoS attacks are relatively low-tech, but they are an effective way to launch a malicious disruption of a network, service, or website by overwhelming it with a massive flood of traffic requests. DoS attacks aim to make websites or networks unavailable to legitimate users for hours or, in rare cases, days.
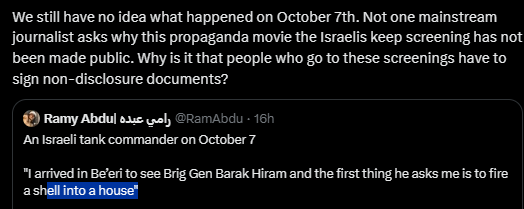
Propaganda and misinformation: This has become the easiest of all cyberwarfare tactics for the average person because it requires almost no technical knowledge and only an internet connection. Additionally, sophisticated bot networks are more prevalent than ever on social media, making it even easier to use this tactic. Attackers can use these same methods against a company or business as an effective tool to sway opinions or harm the reputation and sow distrust with customers, investors, and partners.
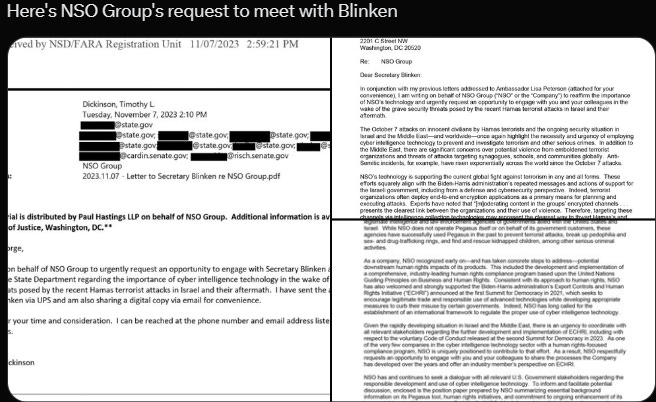
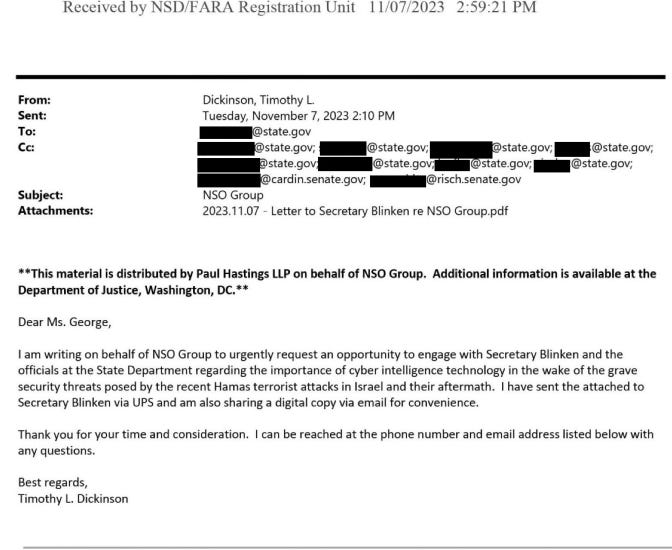
Cyber espionage: State actors or cyber criminals can monitor communications, infiltrating networks, and gain valuable trade or secret information that they can use for a wide range of future attacks. Social engineering campaigns are also often a first step to deploy backdoors that bypass traditional security methods and then gather information through social engineering instead of relying only on bruteforce hacking attempts. The use of hacked systems and data also plays a role in cyber espionage. Once data or an intrusion gets filtered, attacks can use it as a stepping stone for further attacks or targeted campaigns to gain additional espionage capabilities.
Hacking and defacement: Security teams are always worried about hacked data. These hacked records may reveal sensitive personal information that could go far beyond personal security and safety, as the data could include home addresses, contact details, or even the names of family members, which hacktivists can exploit for harassment or additional cyberattacks. Access to private data can offer additional insights into the digital lives of employees or customers and put them at risk for targeted phishing attempts and malware distribution. Security teams monitoring a nation’s defense capabilities always look to ensure the security of personal data whenever they have been involved in a data breach.
Defacing: Attackers often look to deface websites, social media accounts, and digital platforms. They aim to hack the website and convey political messages and ideologies. These attacks are usually done through an SQL injection in which the hacker exploits vulnerabilities in a website’s input fields to manipulate the website’s database. By injecting carefully-crafted SQL queries, an attacker can bypass security measures and gain unauthorized access. This form of attack lets the hacker retrieve confidential user credentials, or take control of the website and deface it. Although these appear to be major incidents, they are not likely to offer the hacker any sensitive data or information because sensitive records are usually not stored on a public-facing website. Usually these credentials are specifically for one area of the website’s administrative panel and, as long as credentials are not reused or shared to access other parts of the network, there’s a lower risk of a serious data breach.
The use of cyberwarfare tactics underscores and defines a new reality of conflicts in the digital age and highlights the importance of addressing these cybersecurity challenges. There are no rules in cyberwarfare, which means attackers consider all types of data fair game and valuable targets. Knowing the methods and tactics of cyberwarfare can help protect people, businesses, and government entities. There has never been a more important time for companies to invest in cyber security, encrypt data, and identify vulnerabilities before bad actors exploit them.
result of QR code = link
I know a lot of high-ranking media, such as New York Times, Guardian, Anadolu, BILD, Spiegel, Financial Times, Strait Times, Washington Post etc subscribed my substack. Plestia ‘Bosbos’ Alaqad ready to be your Stringer inside Gaza under bombing by Israel. Plestiaa2011@gmail.com
Toddler with Plestia, before war, living in Northern Gaza and they evacuated to Southern Gaza. Since Friday, Oct 13, when Israel announced to every Gazans from northern move to southern, more than 5,000 killed in southern, not counting barbaric bombing in northern Gaza. Northern Gaza is being depopulated, while even residents in the south are ordered to evacuate as the israelis implement their ethnic cleansing. Refugee literally fulfilled Israel warning, and still killed with barbaric bombing by Israel. Documentation by Plestia Alaqad
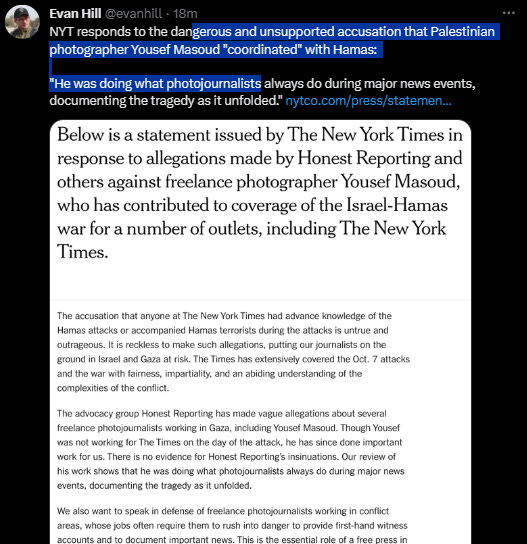
Even, Evan Hill is Washington Post journo, not NYT / New York Times
————————————————
Forgive me for pointing out that my ability to provide this coverage is entirely dependent on your kind voluntary subscriptions which keep this newsletter-substack going. This post is free for anybody to reproduce or republish, including in translation. You are still very welcome to read without subscribing.
Unlike adversaries including the Integrity Initiative, The Atlantic, Visegrad, Bellingcat, the Atlantic Council and hundreds of other warmongering propaganda operations, this newsleter-substack has no source of state, corporate or institutional finance whatsoever. It runs entirely on voluntary subscriptions from its readers – many of whom do not necessarily agree with every article, but welcome the alternative voice, insider information and debate.