Breaking: Cyberattacks China - U.S. and NatSec Adviser Jake Sullivan, Completely Timeline (2018 - July 30, 2023)
Author discovered malware in Fortune 500 company years ago, prevented before suffered more losses. Investigation by Microsoft since May 2023 cannot corroborate its malware was retaliation by China.
4.55pm Canberra (July 30) / 2.55pm Beijing (July 30) / 2.55am Washington DC (July 30) —- this note writing since July 28. Very long / longform about serious cyberattacks.
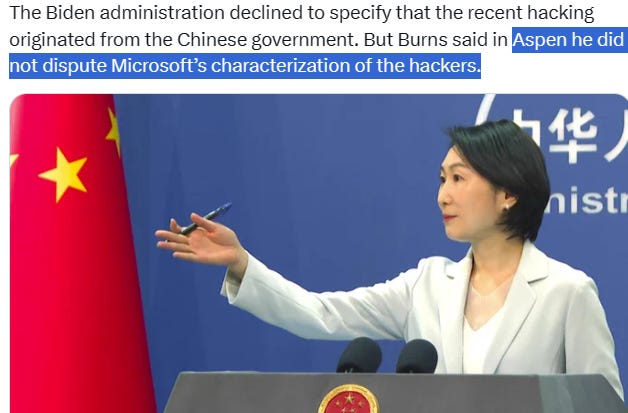
May 16, 2023, the U.S. Secret Service is investigating how a man entered the home of President Biden’s national security adviser Jacob “Jake” Jeremiah Sullivan in the middle of the night roughly two weeks ago without being detected by agents guarding his house. Same day (May 16, 2023), even just separate minutes, Microsoft accused hackers linked to China of accessing the emails of US and other Western officials.
The discovery of the malware has touched off a series of Situation Room meetings in the White House in recent months, as senior officials from the National Security Council, the Pentagon, the Homeland Security Department and the nation’s spy agencies attempt to understand the scope of the problem and plot a response. Between 2017 and May 2020, Jake Sullivan served on an advisory council for Microsoft; in 2020, he was paid $45,000 for this work. Given his role in crafting U.S. cyber security policy in the Biden administration, including overseeing the government's response to January's cyberattack on Microsoft, concerns have been raised about potential conflicts of interest.
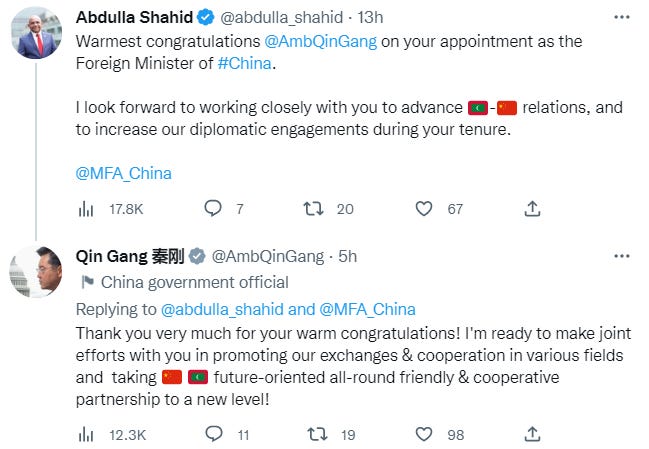
On July 13, 2023 (17 days ago, and around 22 days after former FM Chinese Qin Gang disappeared), the discussions between Secretary of State Antony John Blinken and (actually On July 13 still) former Foreign Minister-but-now-appointed again to be FM Chinese Wang Yi, on the sidelines of the Association of Southeast Asian Nations (ASEAN) summit in Jakarta Indonesia came one day after Microsoft accused hackers linked to China of accessing the emails of US and other Western officials. Also raised U.S. participation in Trans-Pacific Partnership as priority issue. A strategic case needed to be made for it “as an instrument that will allow us to compete more effectively with China.
Wang Yi reappointed again to be FM Chinese since July 24, 2023, after more than 30 days disappeared of Qin Gang. The biggest achievement by Wang Yi is central role to mediate Saudi - Iran, and then, surprisingly, make another “domino-fall”, each other Middle East countries except Israel set a peace, truce.
Beijing has vehemently denied involvement in the hacking operation reported by Microsoft and called the US the “world’s biggest hacking empire and global cyberthief”. Since February 2023 before spy balloon incident, U.S. and China sides quietly try to create “another BALI moment” in San Francisco next November. This year, U.S. is APEC Chairs.
In Jakarta, Blinken told Wang Yi that Washington would hold hackers who target US citizens “accountable”. In Pentagon July 11, top Pentagon official for Indo-Pacific Dr. Ratner met Chinese Ambassador Xie Feng at the Defense Department. Pentagon said in a statement, as military-to-military talks have been stalled for a while. Until I write it, Ambassador Xi Feng not yet uploaded his meeting with Dr. Ratner even until now (July 30). Ambassador Xie choose to upload his meeting with Indonesia Ambassador and another moment. Ambassador Xie actually very active in twitter and (repeatedly) in same day about his meeting, he immediately uploaded on twitter.
Biden administration believes China has implanted malware in key US power & communications networks in a 'ticking time bomb' that could disrupt the military in event of a conflict, notably if Beijing were to move against Taiwan. Important read for those who have somehow missed the many signs: "The coming war with China". Absolutely insane but the US simply cannot conceive of a world which it doesn't dominate, so it's ready to wage war against 1.4 billion people to perpetuate it.
Can confirm that (my country) Indonesia does not seek help or some warning about cyber-infrastructure related with military (not civilian) since May 2023. Try to find out if Australia or New Zealand facing malware too in May-July: zero, or, “actually suffered but keep secret in internal Five Eyes”. Jokowi meet Xi Jinping (July 27, 2023) in Beijing.
June 1, 2018 (5 years 1 month ago), malware used by the United States in offensive cyber-operations plays “nice” when compared to other nation-state malware, according to FireEye CEO Kevin Mandia.
Speaking at the Cyber Threat Intelligence Forum produced by Scoop News Group (June 1, 2018), Mandia said when FireEye analyzes malware from state-backed hackers, the company usually finds elements of public policy baked into operations. Certain tells in the malware’s behavior or the code itself can be indicative of which state is behind it.
“We find malware that sometimes has a time to live and then it doesn’t run anymore. I wonder who would do that,” Mandia said on stage. “Probably [the U.S.] because we’re the nicest hackers in cyberspace, besides maybe China.”
The U.S. and China are more disciplined in their operations than adversaries like North Korea and Russia, who are instead unrestrained, he said.
“We see guardrails on malware from nations like the United States, but do we see guardrails on malware from Russia? No.”
Other experts, including former U.S. officials, contend that the U.S. can be similarly unrestrained and careless in cyberspace. They point to one specific case that’s widely attributed to the U.S. known as “Stuxnet,” which originally targeted but quickly spread beyond an Iranian nuclear enrichment facility.
Mandia went on to describe an unspecified North Korean cyber-operation that when it detected someone was investigating, the malware rewrote the victim’s hard drive. Such properties are indicative of North Korea’s attitude toward systems they compromise, Mandia said.
“That’s annoying to deal with, but that’s a policy decision. They don’t care what they destroy when they compromise something,” he said. “And I have a funny suspicion with our lawyers looking over their shoulders with all of our offensive capability, we absolutely do care and we’re not going to have collateral damage in cyberspace.”
The U.S.’s behavior could change soon. Officials inside the National Security Council are pressing for more offensive measures on the heels of U.S. Cyber Command’s recent elevation to a fully independent combatant command.
“My gut, just pure gut, not fact based — [U.S. Cyber Command] will probably break the niceties,” Mandia explained. “In cyberspace, everyone else is breaking [laws]. Nobody wants to over escalate, however the next war will be fought with a cyber component. We’ll have to be ready for that.”
The public remarks cracked a window into how U.S. cybersecurity companies deal with malware that appears to originate from the U.S. or allied governments.
Mandia, for example, that before publishing a public threat intelligence report, FireEye will typically tip off intelligence officials from the Five Eyes alliance (FVEY -- an intelligence alliance comprising Australia, Canada, New Zealand, the United Kingdom, and the United States) about the release. If FireEye detects malware on a customer’s system that researchers think is from the U.S. or an allied country, it will remove it. But Mandia said such malware ought to be stealthier.
“If friendlies get caught by our detection, then in my opinion is they just need to get better,” Mandia said. “We’re going to protect our clients first and foremost.”
On December 1, 2018 (exactly 6 months after Cyber Threat Intelligence Forum, June 1, 2018), Meng Wanzhou, a Huawei executive, was arrested by Canadian authorities at Vancouver International Airport, in order to face charges of fraud and conspiracy in the United States. China responded by arresting two Canadian nationals. According to the South China Morning Post this conflict was seen by analysts as the beginning of a direct clash between the CCPs leadership of China and members of the Five Eyes alliance. In the months that followed, the United States placed restrictions on technology exchanges with China. Following prompting by parliamentarians in Australia and by US Secretary of State Mike Pompeo, the UK Government announced it would reduce the presence of Huawei technology in its 5G network to zero. The newspaper reported that these events were seen by Beijing as political warfare "waged with the world’s oldest intelligence alliance, the Five Eyes."
In mid-April 2021, the New Zealand Foreign Minister Nanaia Cybele Mahuta issued a statement that New Zealand would not let the Five Eyes alliance dictate its bilateral relationship with China and that New Zealand was uncomfortable with expanding the remit of the intelligence grouping. July 27, 2023 (3 days ago), again from New Zealand FM Nanaia Cybele Mahuta, "I'll be really clear, we're not contemplating joining AUKUS, not only would AUKUS clash with our nuclear-free laws, but also the country's nuclear-free Pacific policy. It's a club we'd have to sell our soul to join.' she said.
In March 2018, Russian cybersecurity company Kaspersky Lab released information on a operation referred to as “Slingshot,” which covered malware that was spying on victims located in the Middle East. Slingshot was a U.S. counterterrorism operation aimed at capturing terrorism targets. Kaspersky’s report subsequently burned the operation.
In a press briefing, FireEye executives said that the company treats all cyberthreats the same, but uses discretion when it comes to public disclosure.
“We respond to breaches all over the world. There are certain times when we think it’s potentially a friendly that was behind it,” said Charles Carmakal, a vice president with Mandiant, FireEye’s incident response subsidiary. “From our investigative perspective we treat it as if it was a threat actor. We help our clients eradicate the threat actor from their environment.”
But even with removing a threat from a customer’s system, officials said the company would stop short of going public. Ron Bushar, a vice president at FireEye, compared the action to publicly disclosing a zero-day vulnerability without giving the affected organization a chance to fix the issue.
“I think there’s a difference between public disclosure and investigative support, and I think there’s important standards or best practices that we tend to follow,” Bushar said. “And certainly before you go public with anything … there has to be a consideration of what the impacts are both from a government perspective and what those impact could be to your client and to the organization conducting those operations.”
Another FireEye executive, John Hultquist, director of threat analysis, said that publicly outing a U.S. cyber-espionage operation, especially a counterterrorism effort, would cross a line that goes beyond quietly dealing with the issue for a client.
“I see counter terrorism stuff all the time,” said Hultquist. “There’s a difference, you know, between stopping it and publishing it for everyone to see.”
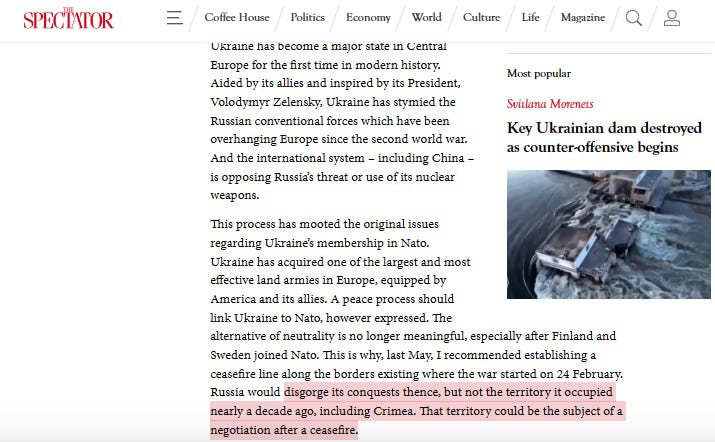
Arguably, U.S. admit failure to analysis in early 2000 about entire Pacific (maybe because too busy in the Middle East), then since 2022 try repair it, in parallel other situation David v Goliath like Taiwan v China (Ukraine v Russia).
Again, June 1, 2018 (5 years 1 month ago), malware used by the United States in offensive cyber-operations plays “nice” when compared to other nation-state malware, according to FireEye CEO Kevin Mandia. So about investigation started in internal Microsoft since May 2023, still very hard to corroborate that its malware was retaliation by China after 2018, or not.
The discovery of the malware has raised fears that Chinese hackers, probably working for the People’s Liberation Army, have inserted code designed to disrupt U.S. military operations in the event of a conflict, including if Beijing moves against Taiwan in coming years.
The malware, one congressional official said, was essentially “a ticking time bomb” that could give China the power to interrupt or slow American military deployments or resupply operations by cutting off power, water and communications to U.S. military bases. But its impact could be far broader, because that same infrastructure often supplies the houses and businesses of ordinary Americans, according to U.S. officials.
The first public hints of the malware campaign began to emerge in late May, when Microsoft said it had detected mysterious computer code in telecommunications systems in Guam, the Pacific island with a vast American air base, and elsewhere in the United States. But that turned out to be only the narrow slice of the problem that Microsoft could see through its networks. The problem about investigation from NYT is, until today (May-July: 3 months), no confirmation by Lockheed Martin about same malware (reported by Microsoft), although (actually) infrastructure in Guam built by Lockheed Martin.
About Guam, actually China and U.S. were a serious incident in last Christmas 2022 (Dec. 25, 2022). The excursions of China's carrier battlegroup Liaoning, during the most recent exercise in the Western Pacific. The carrier battlegroup came within 618 km northwest of Guam (Distance Beijing to Guam: 4,030 - 4,050 km). On Dec. 25 the Liaoning was spotted 670 km (416 miles) southeast of Okinotorishima, before returning to the waters between Taiwan and Japan. By 2025, China can muster a fleet, capable of deterring US naval activities in the Western Pacific. By 2025, China will have 3 carriers in service: Carrier 16 Liaoning, Carrier 17 Shandong, and Carrier 18 Fujian. Another important milestone around 2025, will be the introduction of J-35 carrier-based stealth fighter.
(So far), seriously the U.S. aims to protect Taiwan, actually based on the newest situation about sophisticated infrastructure in Palau, not only Guam (which, according to Microsoft, Guam suffered serious malware). In Palau (*distance Guam to Palau: 1,280 - 1,300 km; distance Beijing to Palau: 4,015 - 4,025 km), Pentagon’s push to drastically beef up both its offensive and defensive capabilities in the Western Pacific gains steam. Called the Tactical Mobile Over-the-Horizon Radar, or TACMOR, the sensor station will be installed on the increasingly strategic island of Palau to enhance air and maritime domain situational awareness for U.S. and allied forces in the region.
A Palauan newspaper publisher entered into a media deal with a company that turned out to have connections to Chinese security services. The deal fell through, but it highlights China’s efforts to influence the Pacific states — including Palau, a U.S. ally and one of the few countries to recognize Taiwan.
For years, Moses Uludong has been a lonely voice pushing the small, strategically located Pacific island nation of Palau towards closer relations with China.
Uludong founded Palau’s first newspaper, Tia Belau, more than five decades ago, back when the archipelago was under U.S. administration.
Now, as tensions rise between China and the West, Uludong thinks Palau could be devastated if war breaks out between the two powers. The nation of 18,000 people became independent in 1994, but is still a close U.S. ally and one of only 13 countries worldwide to defy China by recognizing Taiwan diplomatically.
So, in 2018, Uludong entered into a deal to set up a new media group that he believed would help restore some balance.
What he didn’t realize was that the initiative was backed by investors with ties to China’s police and military, public records obtained by OCCRP show.
The Palau Media Group was the brainchild of an old friend, Tian “Hunter” Hang, an expatriate Chinese hotelier on the island, Uludong told OCCRP. The company was supposed to raise Palau’s profile in China by making it a “hub of information,” he said, bringing news from across the Pacific to a Chinese audience.
“We want to sell Palau, you know, [to get] investment from China,” he said.
Though the new media group had a launch event in Hong Kong, it never fully got off the ground. Nevertheless, the deal appears to have aided in another goal: spreading Chinese influence in the Pacific country. Emails obtained by reporters show that, shortly after launching the venture, Tian used Uludong’s existing newspaper on at least one occasion to publish pro-Chinese content.
Back to TACMOR in Palau. The Department of Defense announced on Dec. 28, 2022 that it had awarded a $118.4 million contract to Gilbane Federal for the construction of reinforced concrete pads and foundations in support of the installation of TACMOR equipment on the island. The contracting activity for what’s being called the TACMOR infrastructure project is the Naval Facilities Engineering Systems Command Pacific, and work is expected to be completed by June 2026. The long-range radar could be critical for keeping an eye on Chinese activities and is another sign of growing U.S. vigilance in the Pacific.
Activities on and around Guam, Tinian, and other U.S. islands in the region have also been conducted. These islands have all become hotspots for U.S. military infrastructure expansion in recent history. Guam specifically is a U.S. territory and the Missile Defense Agency (MDA), the Army, and the Navy have together been working on new air and missile defense capabilities on the island, which can be read about in detail in this past War Zone piece.
In fact, the MDA just awarded Lockheed Martin a contract worth $528 million that expands upon the company’s existing Aegis Weapon System to implement integrated air and missile defense capabilities into an Aegis Guam System. This capability will allow U.S. forces to engage ballistic threats with SM-3 interceptors at various points in the missiles’ flight paths, though other interceptors like the SM-6 and the forthcoming Glide Phase Interceptor could eventually be integrated into Aegis Guam as well.
The future AEGIS Ashore Missile Defense complex being built in Guam will resemble similar sites like the one at the Pacific Missile Range Facility (PMRF) at Kauai, Hawaii. Again, the problem about investigation from NYT is, until today (May-July: 3 months), no confirmation by Lockheed Martin about same malware (reported by Microsoft), although (actually) infrastructure in Guam built by Lockheed Martin.
Japan, under a U.S. Foreign Military Sales (FMS) effort, provided Lockheed Martin with the preliminary rounds of funding for the creation of a SPY-7-compatible AEGIS Ashore. The country had plans to install two SPY-7-equipped AEGIS Ashores, but eventually ran into issues with spiraling funding requirements and plummeting support from the public.
The Japanese AEGIS Ashores were canceled, but the services and equipment that had been funded in support of the land-based AEGIS systems were eventually reimagined and were reconfigured for two sea-based AEGIS vessels. Japanese funding for a SPY-7-based AEGIS capability continues.
For the purpose of the recently announced award, the MDA is obligating an initial round of $11.4 million in Fiscal Year 2023 research, development, test, and evaluation funding at time of the award.
Lockheed Martin’s work will be performed in Moorestown, with period of performance lasting from the time of the award (December 28, 2023) through December 31, 2027.
The U.S. Missile Defense Agency at Dahlgren, Virginia, is performing the role of contracting activity for the program.
These systems are not nearly as precise or resolving as many of their line-of-sight counterparts, and their static nature makes them vulnerable to attack. Atmospheric and space weather conditions also play a big role in their effectiveness from moment to moment. Still, they can offer wide-area situational awareness and critical sensor cueing and early warning, which would allow other higher-resolution sensors without such a long reach or large view to investigate a target further. With networking and data-fusion, this can happen seamlessly. They can also spot stealthy targets that are optimized to evade detection by fire control and traditional line-of-sight search radars operating on higher frequencies.
More than a dozen U.S. officials and industry experts said in interviews over the past two months that the Chinese effort goes far beyond telecommunications systems and predated the May report by at least a year. They said the U.S. government’s effort to hunt down the code, and eradicate it, has been underway for some time. Most spoke on the condition of anonymity to discuss confidential and in some cases classified assessments. Again, this is why (in Jakarta, July 13) Blinken told Wang Yi that Washington would hold hackers who target US citizens “accountable”.
They say the investigations so far show the Chinese effort appears more widespread — in the United States and at American facilities abroad — than they had initially realized. But officials acknowledge that they do not know the full extent of the code’s presence in networks around the world, partly because it is so well hidden.
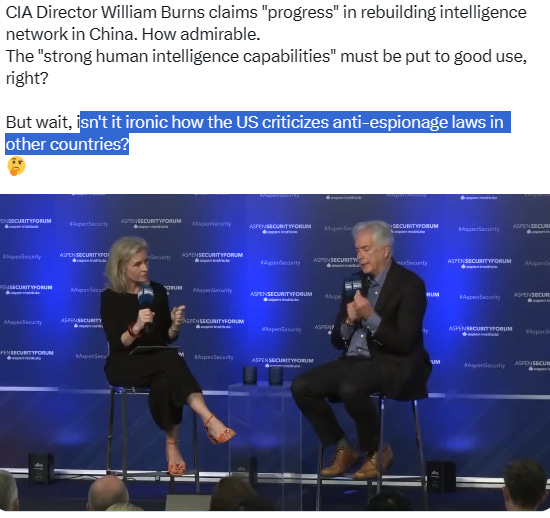
(CIA Director Burns, in ASPEN SECURITY FORUM, repeatedly mentioned China and Microsoft)
In China side, Huawei has ambitious plans to restart the manufacturing of high-end mobile system-on-chips as early as this year, a report by Nikkei claims. The story corroborates an earlier Reuters report that Huawei plans to use SMIC's 7nm-class fabrication technology to make its comeback to smartphone SoCs. But there is a problem that Huawei may reportedly face: high defect density of SMIC's 7nm-class node.
"However, the production yield [quality] for a 7nm node is believed to be quite low, at about 50%, and it still has lots of room for improvement," said Donnie Teng, an analyst with Nomura Securities, in a comment to Nikkei. "The chip being available and the chip being commercially ready are different things. It is still worth monitoring how it goes, but we understand Huawei is willing to invest a lot on this to bring back its chips."
Contemporary mobile SoCs contain tens of billions of transistors and are fairly large. For example, Apple's A16 Bionic comprises of 16 billion of transistors and runs at up to 3.46 GHz. Huawei has historically competed against Apple and Samsung with its flagship smartphones and developed truly advanced SoCs. We do not know what Huawei plans to do at this time, but we are pretty sure that it wants to build something that is competitive enough with high-end smartphones from its rivals.
SMIC has never formally announced its 7nm-class technology, but the node in question could be its N+1 process that was designed as a low-cost alternative to TSMC's N7 and has been in production since at least early 2021. Typically, nodes designed for inexpensive chips are not meant to produce SoCs with large dies. But smartphone SoCs that pack billions of transistors tend to be relatively large, so making them using N+1 may be challenging.
Of course, it is possible that SMIC and Huawei have designed a new node that is optimized for high-performance mobile SoCs and while its defect density may be too high for the target applications now, both companies will work to reduce it and improve yields.
Huawei and SMIC have been blacklisted by the U.S. government since 2020. While Huawei does not have access to TSMC's or Samsung Foundry's process technologies, SMIC cannot obtain fab tools advanced enough to build chips on 14nm-class FinFET process technologies without getting permission from the U.S. government. But SMIC still has equipment that is good enough to make chips on a 5nm-class process technology and while they will likely be more expensive than competing processors produced by TSMC using EUV tools, they will still do the job.
For China, if Huawei can bring its mobile chips back into production, it would represent a significant victory. The country has spent many years and substantial amounts of money to establish a comprehensive domestic chip industry, but SMIC has almost managed to get to 7nm and 5nm-class nodes, it could never obtain EUV equipment to develop more advanced fabrication technologies. Furthermore, without access to contemporary DUV tools its ability to make 14nm and 7nm-class chips is under question.
Back to U.S. side. The discovery of the malware has touched off a series of Situation Room meetings in the White House in recent months, as senior officials from the National Security Council, the Pentagon, the Homeland Security Department and the nation’s spy agencies attempt to understand the scope of the problem and plot a response.
Biden administration officials have begun to brief members of Congress, some state governors and utility companies about the findings, and confirmed some conclusions about the operation in interviews with The New York Times. This investigation by NYT (2.22am Canberra (July 30) / 1.22am Beijing (July 30) / 1.22pm Washington DC (July 29)) just came 13 hours after 4 minister (2+2, US and Australia) giving a statement on the 33rd AUSMIN.
Massive approach by the West (at least U.S. and France) in South Pacific since July 22-July 29:
- President of France Macron giving major speech in Noumea on New Caledonia's political future (now Macron in Sri Lanka)
- Defense Minister Lloyd Austin III arriving in Port Moresby for talks on defence pact
- FM / Secretary of State Antony John Blinken opening new US Embassy in Tonga
- PM Australia Anthony Norman Albanese + PM New Zealand Christopher John Hipkins talks in Wellington. New Zealand will not be joining AUKUS
- Friday, July 28, Antony John Blinken and Lloyd Austin III landed in Brisbane, and meet Australia PM Anthony Norman Albanese
- Saturday, July 29, the 33rd AUSMIN
US counters or rein China's influence in the South Pacific. Western leaders rush to the South Pacific in effort to counter China.
There is a debate inside the administration over whether the goal of the operation is primarily aimed at disrupting the military, or at civilian life more broadly in the event of a conflict. But officials say that the initial searches for the code have focused first on areas with a high concentration of American military bases.
“The Biden administration is working relentlessly to defend the United States from any disruptions to our critical infrastructure, including by coordinating interagency efforts to protect water systems, pipelines, rail and aviation systems, among others,” said Adam R. Hodge, the acting spokesman for the National Security Council.
He added: “The president has also mandated rigorous cybersecurity practices for the first time.” Mr. Hodge was referring to a series of executive orders, some motivated by concerns over SolarWinds, commercial software used widely by the U.S. government that was breached by a Russian surveillance operation, and the Colonial Pipeline ransomware attack by a Russian criminal group. That attack resulted in the temporary cutoff of half the gasoline, jet fuel and diesel supplies that run up the East Coast.
The U.S. government and Microsoft have attributed the recent malware attack to Chinese state-sponsored actors, but the government has not disclosed why it reached that conclusion. There is debate among different arms of the U.S. government about the intent of the intrusions, but not about their source.
The public revelation of the malware operation comes at an especially fraught moment in relations between Washington and Beijing, with clashes that include Chinese threats against Taiwan and American efforts to ban the sale of highly sophisticated semiconductors to the Chinese government. Many of the tensions in the relationship have been driven not only by technological competition but by mutual accusations of malicious activity in cyberspace.
The United States has blamed China for a variety of major hacks against U.S. agencies and infrastructure, and accused the foreign power of spying from a bus-size balloon that traversed the United States in February, until it was shot down off South Carolina. For its part, China has accused the United States of hacking into Huawei, its telecommunications giant. Secret documents released a decade ago by Edward Snowden, a former National Security Agency contractor now in exile in Russia, confirmed that American intelligence agencies did just that.
But almost all of those cases involved intelligence gathering. The discovery of the malicious code in American infrastructure, one of Mr. Biden’s most senior advisers said, “raises the question of what, exactly, they are preparing for.”
If gaining advantage in a Taiwan confrontation is at the heart of China’s intent, slowing down American military deployments by a few days or weeks might give China a window in which it would have an easier time taking control of the island by force.
Chinese concern about American intervention was most likely fueled by President Biden’s several statements over the past 18 months that he would defend Taiwan with American troops if necessary.
Another theory is that the code is intended to distract. Chinese officials, U.S. intelligence agencies have assessed, may believe that during an attack on Taiwan or other Chinese action, any interruptions in U.S. infrastructure could so fixate the attention of American citizens that they would think little about an overseas conflict.
The Chinese embassy in Washington issued a statement on Saturday after publication of this article, denying that it engages in hacking and accusing the United States of being a far larger offender. “We have always firmly opposed and cracked down on all forms of cyberattacking in accordance with the law,” said Haoming Ouyang, an embassy spokesman.
References to Qin Gang are being axed from the Chinese foreign ministry website. But his portrait was still hanging at the Chinese embassy in Washington DC (July 25, 2023)
“The Chinese government agencies face numerous cyberattacks every day, most of which come from sources in the U.S.,” he wrote, adding: “We hope relevant parties will stop smearing China with groundless accusations.”
Chinese officials have never conceded that China was behind the theft of security clearance files of roughly 22 million Americans — including six million sets of fingerprints — from the Office of Personnel Management during the Obama administration. That exfiltration resulted in an agreement between President Obama and President Xi Jinping that resulted in a brief decline in malicious Chinese cyberactivity. The agreement has since collapsed.
Since January 2023, all that has changed drastically between two superpowers, just 47 days after stunning handshake Biden - Xi Jinping in Bali amid G20 Summit 2022 in Indonesia: There is now open talk in Washington about a potential war with China, and soon. To take just one example: In a conversation hosted earlier this year by the Center for Strategic and International Studies, Reps. Mike Waltz (R-Fla.) and Jason Crow (D-Colo.) spoke as if a war with China is highly probable, even guaranteed. Crow went so far as to suggest that the United States abolish any caps on how many of its military personnel in uniform are permitted to work on Taiwan as instructors, war planners, and military attaché.
Such a move—which itself would move the United States and China closer to war—is warranted, according to Crow, because “the cat is out of the bag,” and “it’s very clear we’ve chosen sides.”
In the brewing conflict between Washington and Beijing, all eyes are on Taiwan, but the truth is the island itself doesn’t matter as much in itself as many believe, nor does the threat of Chinese control of its crucial semiconductor sector. After all, China already dominates a massive list of inputs that America needs (rare earths and metals, ordinary metals, electronics, pharmaceutics, machine tools, telecom equipment, and much more besides); one more Chinese-cornered market won’t make or break the US economy. The fate of the population of Taiwan is equally unimportant: Whether 20 million ethnic Chinese pay their taxes to Taipei or Beijing is immaterial to the future of ordinary Americans.
Now, Chinese cyberoperations seem to have taken a turn. The latest intrusions are different from those in the past because disruption, not surveillance, appears to be the objective, U.S. officials say.
At the Aspen Security Forum earlier this month, Rob Joyce, the director of cybersecurity at the National Security Agency, said China’s recent hack targeting the American ambassador to Beijing, Nicholas Burns, and the commerce secretary, Gina Raimondo, was traditional espionage. The spy balloon shot down earlier this year also captured public attention, but generated less concern inside the intelligence community. Intelligence officials and others in the Biden administration viewed those operations as the kind of spy-versus-spy games that Washington and Beijing have run against each other for decades.
In contrast, Mr. Joyce said the intrusions in Guam were “really disturbing” because of their disruptive potential.
The Chinese code, the officials say, appears directed at ordinary utilities that serve both civilian populations and nearby military bases. Only America’s nuclear sites have self-contained communication systems, electricity and water pipelines. (The code has not been found in classified systems. Officials declined to describe the unclassified military networks in which the code has been found.)
While the most sensitive planning is carried out on classified networks, the military routinely uses unclassified, but secure, networks for basic communications, personnel matters, logistics and supply issues.
Officials say that if the malware is activated, it is not clear how effective it would be at slowing an American response — and that the Chinese government may not know, either. In interviews, officials said they believe that in many cases the communications, computer networks and power grids could be quickly restored in a matter of days.
But intelligence analysts have concluded that China may believe there is utility in any disruptive attack that could slow down the U.S. response.
The initial Microsoft discovery in Guam — home to major U.S. Air Force and Marine bases — was attributed by the company to a Chinese state-sponsored hacking group that the company named Volt Typhoon.
A warning from the Homeland Security Department’s Cybersecurity and Infrastructure Security Agency, the National Security Agency and others issued the same day also said the malware was from the state-sponsored Chinese hacking group and was “living off the land.” The phrase means that it was avoiding detection by blending in with normal computer activity, conducted by authorized users. But the warning did not outline other details of the threat.
Some officials briefly considered whether to leave the malware in place, quietly monitor the code they had found and prepare plans to try to neutralize it if it was even activated. Monitoring the intrusions would allow them to learn more about it, and possibly lull the Chinese hackers into a false sense that their penetration had not been exposed.
But senior White House officials quickly rejected that option and said that given the potential threat, the prudent path was to excise the offending malware as quickly as it could be found. Still, there are risks.
American cybersecurity experts are able to remove some of the malware, but some officials said there are concerns that the Chinese could use similar techniques to quickly regain access.
Removing the Volt Typhoon malware also runs the risk of tipping off China’s increasingly talented hacking forces about what intrusions the United States is able to find, and what it is missing. If that happens, China could improve its techniques and be able to reinfect military systems with even harder-to-find software.
The recent Chinese penetrations have been enormously difficult to detect. The sophistication of the attacks limits how much the implanted software is communicating with Beijing, making it difficult to discover. Many hacks are discovered when experts track information being extracted out of a network, or unauthorized accesses are made. But this malware can lay dormant for long periods of time.
Speaking earlier this month at an intelligence summit, George Barnes, the deputy director of the National Security Agency, said the Volt Typhoon attacks demonstrated how much more sophisticated China had become at penetrating government and private sector networks.
Mr. Barnes said that rather than exploit flaws in software to gain access, China had found ways to steal or mimic the credentials of system administrators, the people who run computer networks. Once those are in hand, the Chinese hackers essentially have the freedom to go anywhere in a network and implant their own code.
“China is steadfast and determined to penetrate our governments, our companies, our critical infrastructure,” Mr. Barnes said.
“In the earlier days, China’s cyberoperations activities were very noisy and very rudimentary,” he continued. “They have continued to bring resources, sophistication and mass to their game. So the sophistication continues to increase.”
============END——————
Thank you, as always, for reading. If you have anything like a spark file, or master thought list (spark file sounds so much cooler), let me know how you use it in the comments below.
If you enjoyed this post, please share it.
If a friend sent this to you, you could subscribe here 👇. All content is free, and paid subscriptions are voluntary.